よくあるウェブ攻撃について解説
ウェブ攻撃
インターネット上には無数の攻撃があり、「自分は普通の開発プログラマーで、セキュリティ志向の開発者ではないから」という理由で、基本的なWeb攻撃をマスターしていないことは許されない!?ここでは、一般的なWeb攻撃をいくつか紹介します。
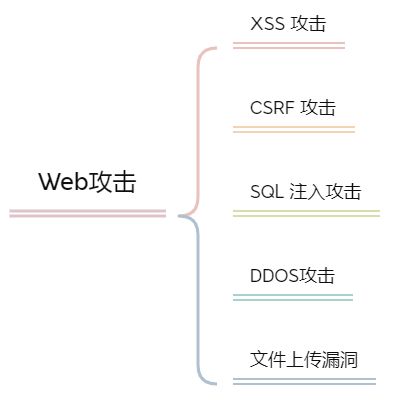
一般的な主なウェブ攻撃は {コード XSS攻撃 {コード /code , {コード {{コード {コード {{コード {{コード {{コード
{{コード {{コード
{{コード {{コード {{コード
{{コード
XSS attacks
{{コード
CSRF attacks
{{コード {{コード クロスサイトスクリプティング攻撃 {{コード
{{コード {{コード クッキー 管理者
{{コード {{コード
{{コード {{コード
{{コード
{{コード
SQL injection attacks
, DDos attack
, File vulnerability attacks
etc. These attacks are not complicated to protect against, but many companies are still subject to the attack, and the source is human negligence.
I. XSS attacks
The full name of the XSS attack is
Cross Site Scripting (CSS)
Why is it not called
CSS
because it's not confused with Cascading Style Sheet (CSS)
XSS attacks
is one of the most common attacks seen in web applications.
Cross-site scripting attacks
, keywords
script
.
Attackers often embed malicious scripts in web pages, which start executing in the background of the client's browser when the user opens the page, often used to steal the client's
cookie
It is often used to steal the client's {{strong cookie}, username and password, download a Trojan horse that executes a virus, and obtain the client's
Admin
permissions.
1. Principle of the attack
The front-end form is commonly used to submit information to the backend
<input type="text" name="username" value="cbuc" />
A very common piece of html code that submits username information to the backend. Under normal circumstances, the user would normally enter their username, which is fine at this point, but under abnormal circumstances, instead of a normal string, the user enters
"/> . By this time the content of the form will be
<input type="text" name="username" value=""/><script> alert("bingo") </script> ;<! -" />
At this time, when the parameters are submitted to the backend, the checks may not pass due to the illegitimacy of the username, and the server will redirect to the page with the above parameters, and a warning box will pop up on the page.

The warning box is not a big problem because, depending on the script, if the attacker modifies it slightly, the nature of it may not be the same ~
Even, the attacker can manipulate the URL, which is normally submitted at
www.xxx.com/login?username="/><script> alert("bingo") </script><! -"
An attacker could encode the URL to confuse the user with.
www.xxx.com/login?username="%2F%3E%3Cscript%3E%20alert(%22bingo%22)%20%3C%2Fscript%3E%3C!-"
2, protection means
Once we know how to attack, it is not difficult to protect ourselves. Since the input parameters are not legitimate, it is necessary to check the input parameters, for example
<, >, ", ", ', '
We need to escape and check these special characters.
Second, CSRF attacks
CSRF attack full name
Cross site request forgery
. It is a malicious exploit of a website. The XSS attack we mentioned above is an attack that takes advantage of trusted users within a site to trigger scripts themselves. CSRF, on the other hand, exploits the attacked site by masquerading as a request from a trusted user.
CSRF attacks, keywords.
forgery
.
This attack steals the identity of the visiting user and sends malicious requests to third-party websites in the visitor's name, often using the visitor's identity to send messages, make transaction transfers, and steal accounts.
1. Principle of the attack
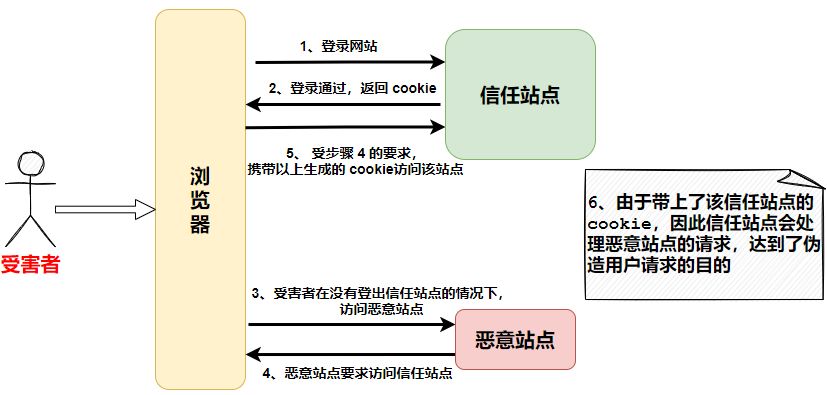
victim
The first step in the
Trusted sites
The cookie will be stored in the browser for a certain period of time. At this point, if the user is not logged out of the
trust site
without logging out of the
malicious site
and this time the malicious site will send a message to the
trust site
This request will carry the above generated cookie, and when the malicious request comes to
trust site
and
Trusted sites
sees the cookie carried by the request, it determines that the request is
victim
was sent. Therefore
trusts the site
will then be based on the
Victims
permissions to complete the
malicious request
command, which could be a command that uses the
victim
s identity to send messages, transfer payments, and so on, so that
malicious site
has achieved the goal of forging
victim
request
Trusted site
The purpose of the
I don't know if you're inspired by seeing this process, and I wonder if the guys in front of the screen have ever
QQ
The experience of being stolen, of course, some of the means of theft is similar to the above process.
This attack is very common in everyday life. If the transfer address of a payment system is
www.xxx.com/pay?accountNum=xxxx&money=xxx
. where accountNum is the account to which the transfer was made and money is the amount transferred. If you happen to have logged in to the payment system and have not logged out in time, you can access the
malicious site
If you click on an image with the following address
<img src="www.xxx.com/pay?accountNum=xxxx&money=xxx" />
While you're browsing through the images with pleasure, you don't know that the specified amount has been quietly deducted from your account at this time!
This is because you did not log out in time
payment system
and then clicked on the
malicious site
which carries your unexpired cookie and successfully steals your money.
2. Protection means
Also know its symptoms and give its medicine! The means of protection are as follows.
1) Set the cookie to HttpOnly
The key to CSRF attacks lies in the use of the user's unexpired cookies, then in order to prevent cookie theft, it is necessary to set the HttpOnly property in the cookie, so that through the program (
XSS attack
) will not be able to read the cookie information, preventing the attacker from forging the cookie.
2) Add token
The protection is still against cookie theft, because all the user authentication information in the request is stored in the cookie, because the key to resist CSRF is: how to put in the request information that the attacker can not forge, and the information can not be stored in the cookie. Then we can add a randomly generated
token
token when the request comes, and if the token does not pass, the request is rejected as a CSRF attack.
3) By Referer
According to the HTTP protocol, there is a field in the HTTP request header called
referer
which records the source address of the Http request. In general, requests to access a security-restricted page all come from the same website.
In CSRF malicious requests are sent from malicious sites, so to defend against CSRF attacks, you need to verify the referer value of each request.
III. SQL Injection Attacks
{SQL Injection
SQL injection is most frequently encountered by programmers. The so-called SQL injection is to achieve the purpose of invasion by passing SQL commands to the server disguised as normal request parameters and tricking the server into eventually executing malicious SQL commands. Attackers often use SQL injection vulnerability to query unauthorized critical information, modify database server data, and change table structure, which is extremely harmful!
1, the principle of the attack
We query the existence of a user often through the following SQL.
SELECT * FROM s_user WHERE username = '' and password = ''
The fatal vulnerability occurs when we query the back end with the following code
Connection con = getConnection();
Statement st = (Statement) con.createStatement();
String sql = "SELECT * FROM s_user WHERE username = '"+ username +"' and password = '"+ passward+"' ";
ResultSet rs = st.executeQuery(sql);
while(rs.next()){
...
}
The logic of the above code is to use the parameters passed in from the front-end to query the database, which at first glance seems to be fine, but at this point if
password
The value passed from the front-end is
' or '1'='1
Then this time the SQL will be
SELECT * FROM s_user WHERE username = '' and password = '' or '1'='1'
You don't have to try this SQL to know that it will find out all the users in the database and return a successful login even though you didn't enter the correct password. And this is a simple and typical SQL injection attack.
' or '1'='1
The hazard is to allow the user to log in password-free if the value passed as
'; drop table xxx; --
This is a big problem!
2. Protection means
1) Use pre-compiled statements
PreparedStatement is an interface in java.sql that inherits from the Statement interface.
The difference between a PreparedStatement and a Statement is that the SQL statement is specified when the PreparedStatement object is created and is immediately sent to the DBMS for compilation, and when the compiled statement needs to be executed, the DBMS runs the compiled SQL statement directly instead of compiling it like other SQL statements:
String sql = "SELECT * FROM s_user WHERE username = ? and password = ? ";
PreparedStatement st = conn.preparedStatement(sql);
st.setString(1, username);
st.setString(2, password);
ResultSet rs = st.executeQUery();
You can see that the original white energy in the SQL statement has been replaced by the placeholder ? has been replaced, and the variables are replaced by
setString()
method.
2) Using the ORM framework
The key means to prevent SQL injection is to escape some keywords, and some common ORM frameworks, such as Mybatis, Hibernate, etc., support escaping the response keywords or special symbols, which can be easily configured to prevent SQL injection vulnerabilities and lower the threshold for ordinary developers to do secure programming.
IV. File Upload Vulnerability
Many websites have upload features, such as uploading images, files, zip packages, and so on. And these resources are often saved on remote servers. A file upload attack means that an attacker takes advantage of the fact that some sites do not do a good job of verifying the file type, uploads an executable file or script, and operates the server with certain permissions through the script, or by inducing external users to access the script file for the purpose of attack.
To prevent users from uploading malicious executable scripts and using the file upload server as a free file storage server, we need to whitelist the type of uploaded files, and limit the size of the uploaded files, and rename the uploaded files so that the attacker cannot guess the access path of the uploaded files.
In this case, we need to whitelist the type of the uploaded file, and we cannot determine the type of the file by the suffix name alone, because the attacker can probably upload the executable file by changing the suffix name to another uploadable suffix name, because we need to use a more secure way to determine the file type.
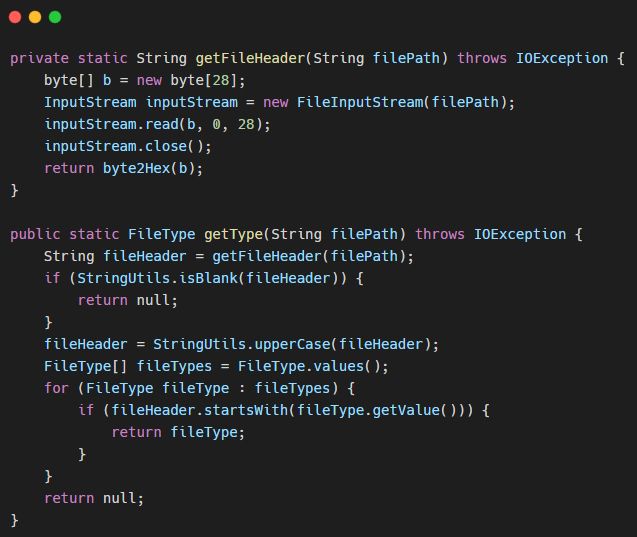
For many types of files, the contents of a few bytes are actually fixed, so the file type can be determined based on the contents of these few bytes, which are also known as the magic number
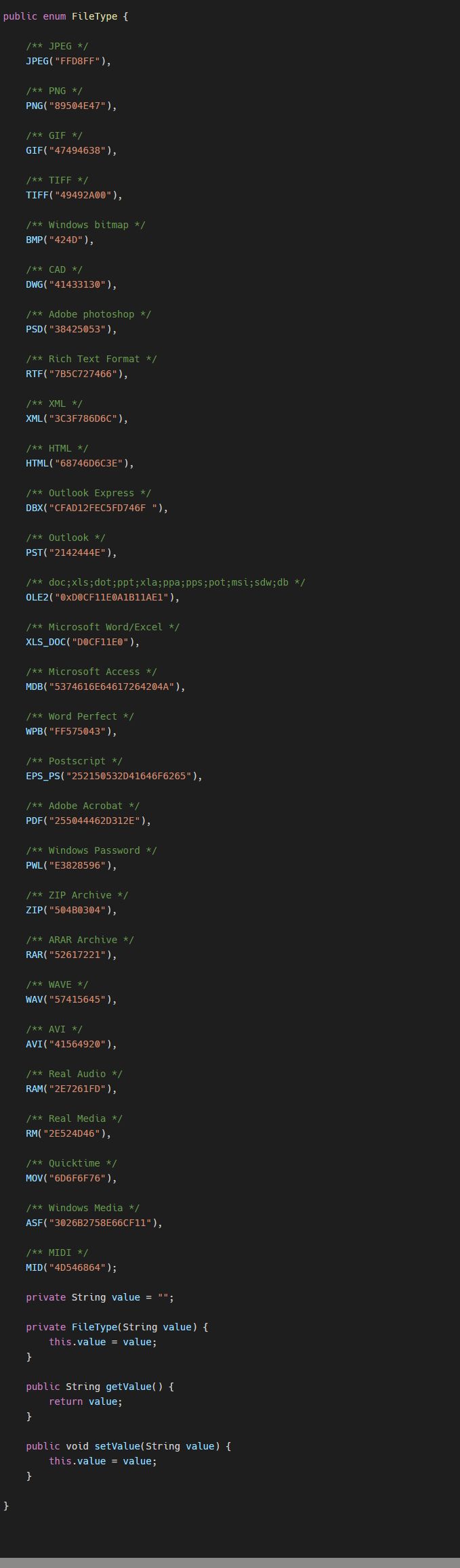
The above is the magic number of file types, and then we can determine the file type by getting the file header and comparing it with the magic number of file types
V. DDOS attack
DDos attack, also known as Distributed Denial of Service (DDOS) attack, is one of the most powerful and difficult to defend against attacks.
The most basic DoS is the use of reasonable client requests to take up too much server resources, so that legitimate users can not get a response from the server. DDoS attacks are a class of attacks based on the traditional DoS attacks. The traditional DoS attack is generally a one-to-one approach, when the attack target's CPU speed, memory or network bandwidth and other performance indicators are not high, its effect is obvious, but with the development of computer and network technology, the computer's processing power increased significantly, the memory continues to increase, which makes the DoS attack gradually lose its effectiveness.
This is similar to the evolution of monolithic applications to distributed architectures, with traditional DoS evolving to distributed DoS (DDoS).
1. Attack principle
DDoS attack refers to the attacker with the help of public networks, a large number of computer equipment combined as an attack platform to launch an attack on one or more targets, so as to achieve the purpose of paralyzing the target host. Usually, before the attack begins, the attacker takes control of a large number of user computers, which are called
Broiler
The attacker will use a large number of computers, called {{code} broilers, to access a host at the same time to paralyze the target host.
2, DDoS classification
DDoS is a means of attack, which is divided into several DDoS attacks
1) SYN Flood
SYN Flood is one of the most classic attacks in the Internet. To understand this attack, we need to start from the process of TCP protocol connection. As we all know, before the TCP protocol can communicate, a connection based on the TCP protocol must be established, and the following is the process of establishing the connection.
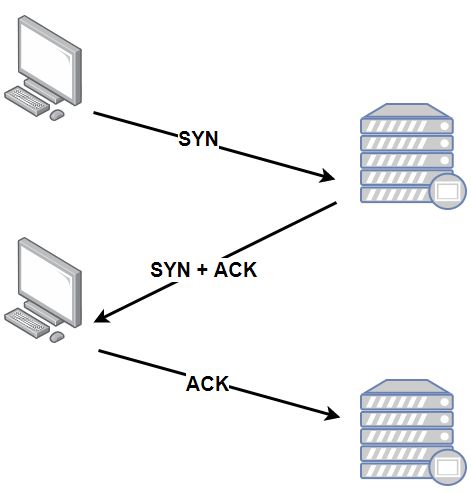
This is a very suggested TCP triple handshake.
- In the first step, the client sends a TCP message containing the SYN identifier, which stands for Synchronized, and the SYN message specifies the client's port number and the initial sequence number of the TCP connection
- In the second step, after receiving the SYN message from the client, the server returns a SYN+ACK message, indicating that the client's request was received and the TCP sequence number was added by 1, ACK means Acknowledgment
- In the third step, after the client receives the SYN + ACK message from the server, it also returns an ACK message to the server, and again, the TCP sequence number is added by 1, at which point the TCP connection is established, and data communication can then take place.
{The TCP protocol is a reliable transport protocol.
The TCP protocol is a reliable transport protocol with some exception handling mechanisms set up during the three handshakes. If the server does not receive the ACK message from the client in the third step, the server will generally retry, that is, send the SYN + ACK message to the client again and keep it in the SYN_RECV state, adding the client to the wait list; on the other hand, after the server sends the SYN + ACK message, it will pre-allocate some resources to the TCP connection to be established, and this On the other hand, after the server sends out a SYN + ACK message, it will pre-allocate some resources to the TCP connection to be established, and this resource will be reserved during the waiting period for retry. Due to the limited resources of the server, it will not receive new SYN messages after the waiting list exceeds the limit, that is, it will refuse to establish new TCP connections.
At this point we can talk about what SYN Flood is all about. SYN Flood uses the TCP protocol's three handshake processes to achieve the purpose of the attack. The attacker forges a large number of IP addresses to send SYN messages to the server, because the forged IP addresses cannot exist, it is impossible to get any response from the client, it will always be stuck in the third step, the server has to maintain a very large half-connection waiting list, and constantly traverse the IP addresses in this list to retry, taking up a lot of system resources. And because of the server's limited resources, malicious connections fill up the server's waiting queue, causing the server to stop receiving new SYN requests and preventing normal users from completing their communications.
2) DNS Query Flood
DNS Query Flood is actually a UDP Fl
{{コード
{{コード
{{コード
{{コード
The full name of the XSS attack is
Cross Site Scripting (CSS)
{{コード
CSS
{{コード
script
{{コード
1. Principle of the attack
{{コード
{{コード
<input type="text" name="username" value="cbuc" />
{{コード
{{コード
<input type="text" name="username" value=""/><script> alert("bingo") </script> ;<! -" />
{{コード {{コード
{{コード {{コード {{コード {コード {コード {コード
{{コード {{コード
{{コード {{コード {{コード
{{コード
{{コード
<input type="text" name="username" value=""/><script> alert("bingo") </script> ;<! -" />
{{コード
The warning box is not a big problem because, depending on the script, if the attacker modifies it slightly, the nature of it may not be the same ~
{{コード {{コード
{{コード
www.xxx.com/login?username="/><script> alert("bingo") </script><! -"
{{コード {{コード 被害者 信頼できるサイト トラストサイト 悪質サイト トラストサイト トラストサイト 信頼できるサイト 被害者 サイトを信頼する 被害者 悪質な要求 ビクティム 悪質サイト 被害者 信頼できるサイト
{{コード
{{コード
2, protection means
{{コード
{{コード
Second, CSRF attacks
{{コード
{{コード
{{コード
CSRF attack full name
Cross site request forgery
. It is a malicious exploit of a website. The XSS attack we mentioned above is an attack that takes advantage of trusted users within a site to trigger scripts themselves. CSRF, on the other hand, exploits the attacked site by masquerading as a request from a trusted user.
Cross site request forgery
{{コード
{{コード
CSRF attacks, keywords.
{{コード
forgery
.
{{コード {{コード
{{コード
This attack steals the identity of the visiting user and sends malicious requests to third-party websites in the visitor's name, often using the visitor's identity to send messages, make transaction transfers, and steal accounts.
{{コード

{{コード
{{コード
I don't know if you're inspired by seeing this process, and I wonder if the guys in front of the screen have ever
QQ
The experience of being stolen, of course, some of the means of theft is similar to the above process.
{{コード
This attack is very common in everyday life. If the transfer address of a payment system is
www.xxx.com/pay?accountNum=xxxx&money=xxx
. where accountNum is the account to which the transfer was made and money is the amount transferred. If you happen to have logged in to the payment system and have not logged out in time, you can access the
malicious site
If you click on an image with the following address
{{コード
{{コード
<img src="www.xxx.com/pay?accountNum=xxxx&money=xxx" />
{{コード
While you're browsing through the images with pleasure, you don't know that the specified amount has been quietly deducted from your account at this time!
{{コード
{{コード
This is because you did not log out in time
payment system
and then clicked on the
malicious site
which carries your unexpired cookie and successfully steals your money.
{{コード {{コード {コード
{{コード
2. Protection means
{{コード {{コード
{{コード {{コード1、攻撃の原理
以下のようなSQLで、よくユーザーの存在を問い合わせます。
1) Set the cookie to HttpOnly
致命的な脆弱性は、以下のコードでバックエンドに問い合わせをしたときに発生します。
The key to CSRF attacks lies in the use of the user's unexpired cookies, then in order to prevent cookie theft, it is necessary to set the HttpOnly property in the cookie, so that through the program (
XSS attack
) will not be able to read the cookie information, preventing the attacker from forging the cookie.
上記のコードのロジックは、フロントエンドから渡されたパラメータを使ってデータベースに問い合わせるというもので、一見すると問題ないように見えますが、この時点でもし
2) Add token
フロントエンドから渡された値は
3) By Referer
すると、今回のSQLは
referer
このSQLを試すまでもなく、データベース内のすべてのユーザーを見つけ出し、正しいパスワードを入力していないにもかかわらず、ログインに成功したことを返すことがわかります。そして、これは単純で典型的なSQLインジェクション攻撃です。
{{コード
として渡された値であれば、パスワードなしでログインできるようになる危険性があります。
In CSRF malicious requests are sent from malicious sites, so to defend against CSRF attacks, you need to verify the referer value of each request.
これは大問題です!
2. 保護とは
1) プリコンパイルされたステートメントを使用する
PreparedStatementはjava.sqlのStatementインターフェイスを継承したインターフェイスです。
PreparedStatementとStatementの違いは、PreparedStatementオブジェクトが生成されるときにSQL文が指定され、すぐにDBMSに送られてコンパイルされ、コンパイルされた文を実行する必要がある場合、他のSQL文のようにコンパイルするのではなく、DBMSが直接コンパイル済みのSQL文を実行する点です。
{SQL Injection
SQL injection is most frequently encountered by programmers. The so-called SQL injection is to achieve the purpose of invasion by passing SQL commands to the server disguised as normal request parameters and tricking the server into eventually executing malicious SQL commands. Attackers often use SQL injection vulnerability to query unauthorized critical information, modify database server data, and change table structure, which is extremely harmful!
1, the principle of the attack
We query the existence of a user often through the following SQL.
SELECT * FROM s_user WHERE username = '' and password = ''
The fatal vulnerability occurs when we query the back end with the following code
Connection con = getConnection();
Statement st = (Statement) con.createStatement();
String sql = "SELECT * FROM s_user WHERE username = '"+ username +"' and password = '"+ passward+"' ";
ResultSet rs = st.executeQuery(sql);
while(rs.next()){
...
}
The logic of the above code is to use the parameters passed in from the front-end to query the database, which at first glance seems to be fine, but at this point if
password
The value passed from the front-end is
' or '1'='1
Then this time the SQL will be
SELECT * FROM s_user WHERE username = '' and password = '' or '1'='1'
You don't have to try this SQL to know that it will find out all the users in the database and return a successful login even though you didn't enter the correct password. And this is a simple and typical SQL injection attack.
' or '1'='1
The hazard is to allow the user to log in password-free if the value passed as
'; drop table xxx; --
This is a big problem!
2. Protection means
1) Use pre-compiled statements
PreparedStatement is an interface in java.sql that inherits from the Statement interface.
The difference between a PreparedStatement and a Statement is that the SQL statement is specified when the PreparedStatement object is created and is immediately sent to the DBMS for compilation, and when the compiled statement needs to be executed, the DBMS runs the compiled SQL statement directly instead of compiling it like other SQL statements:
String sql = "SELECT * FROM s_user WHERE username = ? and password = ? ";
PreparedStatement st = conn.preparedStatement(sql);
st.setString(1, username);
st.setString(2, password);
ResultSet rs = st.executeQUery();
You can see that the original white energy in the SQL statement has been replaced by the placeholder ? has been replaced, and the variables are replaced by
setString()
method.
2) Using the ORM framework
The key means to prevent SQL injection is to escape some keywords, and some common ORM frameworks, such as Mybatis, Hibernate, etc., support escaping the response keywords or special symbols, which can be easily configured to prevent SQL injection vulnerabilities and lower the threshold for ordinary developers to do secure programming.
IV. File Upload Vulnerability
Many websites have upload features, such as uploading images, files, zip packages, and so on. And these resources are often saved on remote servers. A file upload attack means that an attacker takes advantage of the fact that some sites do not do a good job of verifying the file type, uploads an executable file or script, and operates the server with certain permissions through the script, or by inducing external users to access the script file for the purpose of attack.
To prevent users from uploading malicious executable scripts and using the file upload server as a free file storage server, we need to whitelist the type of uploaded files, and limit the size of the uploaded files, and rename the uploaded files so that the attacker cannot guess the access path of the uploaded files.
In this case, we need to whitelist the type of the uploaded file, and we cannot determine the type of the file by the suffix name alone, because the attacker can probably upload the executable file by changing the suffix name to another uploadable suffix name, because we need to use a more secure way to determine the file type.
For many types of files, the contents of a few bytes are actually fixed, so the file type can be determined based on the contents of these few bytes, which are also known as the magic number

The above is the magic number of file types, and then we can determine the file type by getting the file header and comparing it with the magic number of file types

V. DDOS attack
DDos attack, also known as Distributed Denial of Service (DDOS) attack, is one of the most powerful and difficult to defend against attacks.
The most basic DoS is the use of reasonable client requests to take up too much server resources, so that legitimate users can not get a response from the server. DDoS attacks are a class of attacks based on the traditional DoS attacks. The traditional DoS attack is generally a one-to-one approach, when the attack target's CPU speed, memory or network bandwidth and other performance indicators are not high, its effect is obvious, but with the development of computer and network technology, the computer's processing power increased significantly, the memory continues to increase, which makes the DoS attack gradually lose its effectiveness.
This is similar to the evolution of monolithic applications to distributed architectures, with traditional DoS evolving to distributed DoS (DDoS).
1. Attack principle
DDoS attack refers to the attacker with the help of public networks, a large number of computer equipment combined as an attack platform to launch an attack on one or more targets, so as to achieve the purpose of paralyzing the target host. Usually, before the attack begins, the attacker takes control of a large number of user computers, which are called
Broiler
The attacker will use a large number of computers, called {{code} broilers, to access a host at the same time to paralyze the target host.
2, DDoS classification
DDoS is a means of attack, which is divided into several DDoS attacks
1) SYN Flood
SYN Flood is one of the most classic attacks in the Internet. To understand this attack, we need to start from the process of TCP protocol connection. As we all know, before the TCP protocol can communicate, a connection based on the TCP protocol must be established, and the following is the process of establishing the connection.

This is a very suggested TCP triple handshake.
- In the first step, the client sends a TCP message containing the SYN identifier, which stands for Synchronized, and the SYN message specifies the client's port number and the initial sequence number of the TCP connection
- In the second step, after receiving the SYN message from the client, the server returns a SYN+ACK message, indicating that the client's request was received and the TCP sequence number was added by 1, ACK means Acknowledgment
- In the third step, after the client receives the SYN + ACK message from the server, it also returns an ACK message to the server, and again, the TCP sequence number is added by 1, at which point the TCP connection is established, and data communication can then take place.
{The TCP protocol is a reliable transport protocol.
The TCP protocol is a reliable transport protocol with some exception handling mechanisms set up during the three handshakes. If the server does not receive the ACK message from the client in the third step, the server will generally retry, that is, send the SYN + ACK message to the client again and keep it in the SYN_RECV state, adding the client to the wait list; on the other hand, after the server sends the SYN + ACK message, it will pre-allocate some resources to the TCP connection to be established, and this On the other hand, after the server sends out a SYN + ACK message, it will pre-allocate some resources to the TCP connection to be established, and this resource will be reserved during the waiting period for retry. Due to the limited resources of the server, it will not receive new SYN messages after the waiting list exceeds the limit, that is, it will refuse to establish new TCP connections.
At this point we can talk about what SYN Flood is all about. SYN Flood uses the TCP protocol's three handshake processes to achieve the purpose of the attack. The attacker forges a large number of IP addresses to send SYN messages to the server, because the forged IP addresses cannot exist, it is impossible to get any response from the client, it will always be stuck in the third step, the server has to maintain a very large half-connection waiting list, and constantly traverse the IP addresses in this list to retry, taking up a lot of system resources. And because of the server's limited resources, malicious connections fill up the server's waiting queue, causing the server to stop receiving new SYN requests and preventing normal users from completing their communications.
2) DNS Query Flood
DNS Query Flood is actually a UDP Fl
SQL文の元の白いエネルギーが、プレースホルダーの ? に置き換えられていること、変数が
Connection con = getConnection();
Statement st = (Statement) con.createStatement();
String sql = "SELECT * FROM s_user WHERE username = '"+ username +"' and password = '"+ passward+"' ";
ResultSet rs = st.executeQuery(sql);
while(rs.next()){
...
}
メソッドを使用します。
2) ORMフレームワークの利用
SQLインジェクションを防ぐ重要な手段は、いくつかのキーワードをエスケープすることです。Mybatis、Hibernateなどの一般的なORMフレームワークは、応答キーワードや特殊記号のエスケープをサポートしており、簡単に設定することでSQLインジェクション脆弱性を防ぎ、一般の開発者が安全なプログラミングをするための敷居を低くすることができます。
IV. ファイルアップロードの脆弱性
多くのWebサイトでは、画像やファイル、ZIPパッケージなどをアップロードする機能があります。そして、これらのリソースは、しばしばリモートサーバーに保存されます。ファイルアップロード攻撃とは、一部のサイトがファイルの種類をうまく確認できないことを利用して、実行ファイルやスクリプトをアップロードし、そのスクリプトを通じて特定の権限でサーバーを操作したり、外部ユーザーを誘導して、攻撃目的のスクリプトファイルにアクセスさせたりすることを指します。
ユーザーが悪意のある実行スクリプトをアップロードし、ファイルアップロードサーバーを無料ファイル保管サーバーとして利用することを防ぐため、アップロードするファイルの種類をホワイトリスト化し、アップロードするファイルのサイズを制限し、攻撃者がアップロードしたファイルのアクセスパスを推測できないようにアップロードしたファイルの名前を変更する必要があります。
この場合、アップロードされるファイルの種類をホワイトリストに登録する必要があり、サフィックス名だけではファイルの種類を判断できません。攻撃者はおそらくサフィックス名を別のアップロード可能なサフィックス名に変更して実行ファイルをアップロードできるため、より安全な方法でファイルの種類を判断する必要があるのです。
多くの種類のファイルでは、数バイトの内容が実は決まっているので、この数バイトの内容からファイルの種類を判定することができ、これはマジックナンバーとも呼ばれています

上記はファイルタイプのマジックナンバーであり、ファイルヘッダを取得してファイルタイプのマジックナンバーと比較することで、ファイルタイプを決定することができます

V. DDOS攻撃
DDos攻撃は、分散サービス妨害(DDOS)攻撃とも呼ばれ、最も強力で防御が困難な攻撃の一つです。
最も基本的なDoSは、合理的なクライアントリクエストを利用してサーバーリソースを過剰に占有させ、正規のユーザーがサーバーから応答を得られないようにすることです。DDoS攻撃は、従来のDoS攻撃をベースにした攻撃の一種です。従来のDoS攻撃は、一般的に1対1のアプローチで、攻撃対象のCPU速度、メモリやネットワークの帯域幅などの性能指標が高くない場合、その効果は明らかですが、コンピュータとネットワーク技術の発展に伴い、コンピュータの処理能力が大幅に増加し、メモリも増加し続け、DoS攻撃は徐々にその効果を失いました。
これは、モノリシックなアプリケーションが分散型アーキテクチャに進化し、従来のDoSが分散型DoS(DDoS)に進化したのと同様である。
1. 攻撃原理
DDoS攻撃再
関連
-
優れたWebログセキュリティ解析ツール10選 おすすめまとめ
-
QQは、履歴を削除する方法簡単な方法を復元するためにチャット
-
ASP、PHP、.NETのHTTP-REFERERの偽造方法と偽造REFERERを防止するための方法
-
WebサイトにおけるInvisible Bomb eWebEditorのファイルアップロードの脆弱性に対するパッチについて
-
PHPSHELLがまた新しくなりました
-
asp cer cdx htrファイルのアップロードを許可しないサイトでの解決策!
-
Macでmitmproxyを使ってHTTPSのデータを取得する方法
-
Sql2005インジェクションアシストスクリプト[修正版]について
-
サーブユーが管理者パスワードを入手する新手口(スピン)
-
Dでよく使われるインジェクションコマンドをいくつかまとめてみました。
最新
-
nginxです。[emerg] 0.0.0.0:80 への bind() に失敗しました (98: アドレスは既に使用中です)
-
htmlページでギリシャ文字を使うには
-
ピュアhtml+cssでの要素読み込み効果
-
純粋なhtml + cssで五輪を実現するサンプルコード
-
ナビゲーションバー・ドロップダウンメニューのHTML+CSSサンプルコード
-
タイピング効果を実現するピュアhtml+css
-
htmlの選択ボックスのプレースホルダー作成に関する質問
-
html css3 伸縮しない 画像表示効果
-
トップナビゲーションバーメニュー作成用HTML+CSS
-
html+css 実装 サイバーパンク風ボタン