管理者ユーザーを作成するためのdosnetの実装
2022-02-09 06:28:50
1. dosコマンドのnetコマンドは、一般的にユーザーを作成します
次のコードは、Administrator ユーザーを作成するために使用されます。
コードです。
// Start the process
DWORD ProcessStartAsUser(char * pProcessPath, char * pCommandLine)
{
DWORD dwProcessID = 0; // Process ID of the new process
try
{
BOOL bResult = FALSE; // return value
PROCESS_INFORMATION pi = { 0 }; // Information about the newly created process
STARTUPINFO si = { 0 }; // Main window characteristics of the new process
DWORD dwSessionId = 0; // currently active session ID
DWORD dwWinlogon = 0; // winlogon process ID
DWORD dwCreationFlags = -1; // creation flags
HANDLE hUserToken = NULL;
HANDLE hUserTokenDup = NULL;
HANDLE hPToken = NULL;
HANDLE hProcess = NULL;
// Get the session ID of the current activity.
dwSessionId = WTSGetActiveConsoleSessionId();
// Create a snapshot of the process
PROCESSENTRY32 procEntry = { 0 };
HANDLE hSnap = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, 0);
if (hSnap == INVALID_HANDLE_VALUE)
{
return 0;
}
// Iterate through the process snapshots, displaying information about each process in turn
procEntry.dwSize = sizeof(PROCESSENTRY32);
bResult = Process32First(hSnap, &procEntry);
if (FALSE == bResult)
{
return 0;
}
do
{
if (strncmp(procEntry.szExeFile, "winlogon.exe", sizeof("winlogon.exe")) == 0)
{
// find the process ID corresponding to the winlogon.exe process
DWORD winlogonSessId = 0;
if (ProcessIdToSessionId(procEntry.th32ProcessID, &winlogonSessId)
&& winlogonSessId == dwSessionId)
{
dwWinlogon = procEntry.th32ProcessID;
break;
}
}
} while (Process32Next(hSnap, &procEntry));
// Get the token by the session ID
bResult = WTSQueryUserToken(dwSessionId, &hUserToken);
if (FALSE == bResult)
{
return 0;
}
dwCreationFlags = NORMAL_PRIORITY_CLASS | CREATE_NEW_CONSOLE;
si.cb = sizeof(STARTUPINFO);
si.lpDesktop = "winsta0\\\default";
TOKEN_PRIVILEGES tp = { 0 };
LUID luid = { 0 }; // system permissions
hProcess = OpenProcess(MAXIMUM_ALLOWED, FALSE, dwWinlogon);
bResult = ::OpenProcessToken(hProcess, TOKEN_ADJUST_PRIVILEGES | TOKEN_QUERY
| TOKEN_DUPLICATE | TOKEN_ASSIGN_PRIMARY | TOKEN_ADJUST_SESSIONID
| TOKEN_READ | TOKEN_WRITE, &hPToken);
if (FALSE == bResult)
{
return 0;
}
// Check the privilege value of the system privilege
bResult = LookupPrivilegeValue(NULL, SE_DEBUG_NAME, &lud);
if (FALSE == bResult)
{
return 0;
}
tp.PrivilegeCount = 1;
tp.Privileges[0].Luid = luid;
Attributes = SE_PRIVILEGE_ENABLED. tp.Privileges[0];
// Create a new access token to duplicate an already existing token
bResult = DuplicateTokenEx(hPToken, MAXIMUM_ALLOWED, NULL,
SecurityIdentification, TokenPrimary, &hUserTokenDup);
if (FALSE == bResult)
{
return 0;
}
// Enable privileged access to the token
bResult = AdjustTokenPrivileges(hUserTokenDup, FALSE, &tp, sizeof(TOKEN_PRIVILEGES),
(PTOKEN_PRIVILEGES)NULL, NULL);
if (FALSE == bResult || GetLastError() == ERROR_NOT_ALL_ASSIGNED)
{
return 0;
}
// Create environment information
LPVOID pEnv = NULL;
if (CreateEnvironmentBlock(&pEnv, hUserTokenDup, TRUE))
{
dwCreationFlags |= CREATE_UNICODE_ENVIRONMENT;
}
else
{
pEnv = NULL;
}
// Create a process via winlogon
bResult = CreateProcessAsUser(
hUserTokenDup, // token
pProcessPath, // full path to the program
pCommandLine, // program command line (either one or the former)
NULL, // process-safe property
NULL, // thread-safe attribute
FALSE, // handle is not inheritable
dwCreationFlags, // creation flags
pEnv, // environment information
NULL, // current path
&si, // main window characteristics of the new process
&pi // information about the newly created process
);
if ((0 ! = GetLastError()) || (false == bResult))
{
}
dwProcessID = pi.dwProcessId;
// Release the handle resource
CloseHandle(hProcess);
CloseHandle(hPToken);
CloseHandle(hUserTokenDup);
CloseHandle(hUserToken);
}
catch (...)
{
}
return dwProcessID;
}
コード解析です。
// Start the process
DWORD ProcessStartAsUser(char * pProcessPath, char * pCommandLine)
{
DWORD dwProcessID = 0; // Process ID of the new process
try
{
BOOL bResult = FALSE; // return value
PROCESS_INFORMATION pi = { 0 }; // Information about the newly created process
STARTUPINFO si = { 0 }; // Main window characteristics of the new process
DWORD dwWinlogon = 0; // winlogon process ID
DWORD dwCreationFlags = -1; // creation flag
HANDLE hUserToken = NULL;
HANDLE hUserTokenDup = NULL;
HANDLE hPToken = NULL;
HANDLE hProcess = NULL;
// Create a snapshot of the process
PROCESSENTRY32 procEntry = { 0 };
HANDLE hSnap = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, 0);
if (hSnap == INVALID_HANDLE_VALUE)
{
return 0;
}
// Iterate through the process snapshots, displaying information about each process in turn
procEntry.dwSize = sizeof(PROCESSENTRY32);
bResult = Process32First(hSnap, &procEntry);
if (FALSE == bResult)
{
return 0;
}
do
{
if (strncmp(procEntry.szExeFile, "winlogon.exe", sizeof("winlogon.exe")) == 0)
{
// find the process ID corresponding to the winlogon.exe process
DWORD dwSessionId = 0;
ProcessIdToSessionId(procEntry.th32ProcessID, &dwSessionId);
dwWinlogon = procEntry.th32ProcessID;
break;
}
} while (Process32Next(hSnap, &procEntry));
dwCreationFlags = NORMAL_PRIORITY_CLASS | CREATE_NEW_CONSOLE;
si.cb = sizeof(STARTUPINFO);
si.lpDesktop = "winsta0\\\default";
TOKEN_PRIVILEGES tp = { 0 };
LUID luid = { 0 }; // system permissions
hProcess = OpenProcess(PROCESS_QUERY_INFORMATION, FALSE, dwWinlogon);
if (NULL == hProcess)
{
return 0;
}
bResult = ::OpenProcessToken(hProcess, TOKEN_ADJUST_PRIVILEGES | TOKEN_QUERY
| TOKEN_DUPLICATE | TOKEN_ASSIGN_PRIMARY | TOKEN_ADJUST_SESSIONID
| TOKEN_READ | TOKEN_WRITE, &hPToken);
if (FALSE == bResult)
{
return 0;
}
// Check the privilege value of the system privilege
bResult = LookupPrivilegeValue(NULL, SE_DEBUG_NAME, &lud);
if (FALSE == bResult)
{
return 0;
}
tp.PrivilegeCount = 1;
tp.Privileges[0].Luid = luid;
Attributes = SE_PRIVILEGE_ENABLED. tp.Privileges[0];
// Create a new access token to duplicate an already existing token
bResult = DuplicateTokenEx(hPToken, MAXIMUM_ALLOWED, NULL,
SecurityIdentification, TokenPrimary, &hUserTokenDup);
if (FALSE == bResult)
{
return 0;
}
// Enable privileged access to the token
bResult = AdjustTokenPrivileges(hUserTokenDup, FALSE, &tp, sizeof(TOKEN_PRIVILEGES),
(PTOKEN_PRIVILEGES)NULL, NULL);
if (FALSE == bResult || GetLastError() == ERROR_NOT_ALL_ASSIGNED)
{
return 0;
}
// Create environment information
LPVOID pEnv = NULL;
if (CreateEnvironmentBlock(&pEnv, hUserTokenDup, TRUE))
{
dwCreationFlags |= CREATE_UNICODE_ENVIRONMENT;
}
else
{
pEnv = NULL;
}
// Create a process via winlogon
bResult = CreateProcessAsUser(
hUserTokenDup, // token
pProcessPath, // full path to the program
pCommandLine, // program command line (either one or the former)
NULL, // process-safe property
NULL, // thread-safe attribute
FALSE, // handle is not inheritable
dwCreationFlags, // creation flags
pEnv, // environment information
NULL, // current path
&si, // main window characteristics of the new process
&pi // information about the newly created process
);
if ((0 ! = GetLastError()) || (false == bResult))
{
}
dwProcessID = pi.dwProcessId;
// Release the handle resource
CloseHandle(hProcess);
CloseHandle(hPToken);
CloseHandle(hUserTokenDup);
}
catch (...)
{
}
return dwProcessID;
}
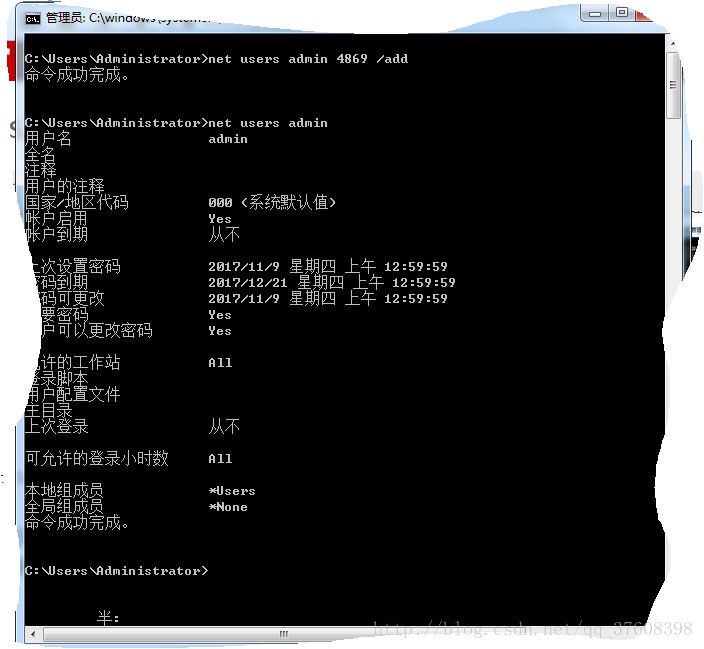
このコマンドは、パスワードが 4869 である標準ユーザー admin を作成します。
作成する前に
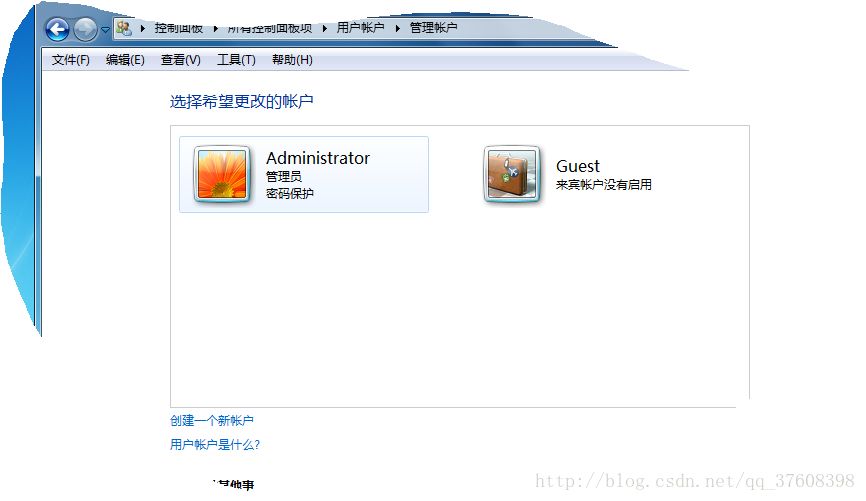
作成後
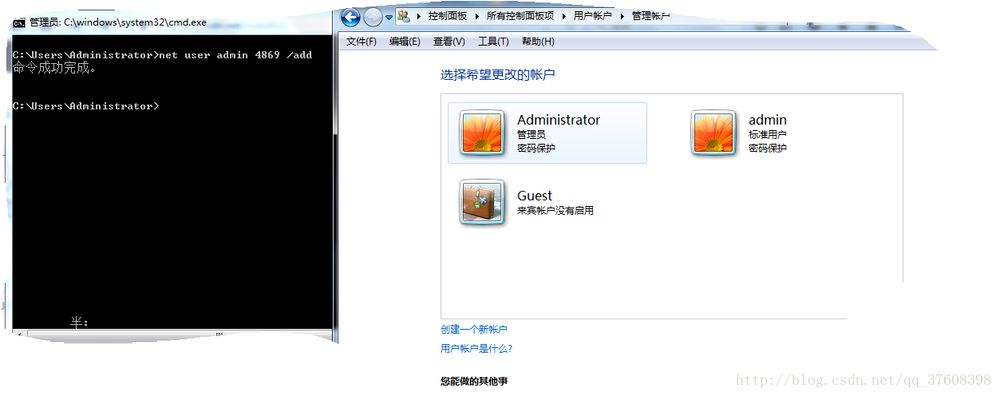
備考 : ここで、パスワード付きのユーザーを作りたくない場合は、以下のようにします。
net users admin /add
net localgroup Administrators admin /add
NET
[ ACCOUNTS | COMPUTER | CONFIG | CONTINUE | FILE | GROUP | HELP
HELPMSG | LOCALGROUP | PAUSE | SESSION | SHARE | START | STATISTICS | STOP | TIME | USE | USER | VIEW ]
STATISTICS | STOP | TIME | USE | USER | VIEW ]
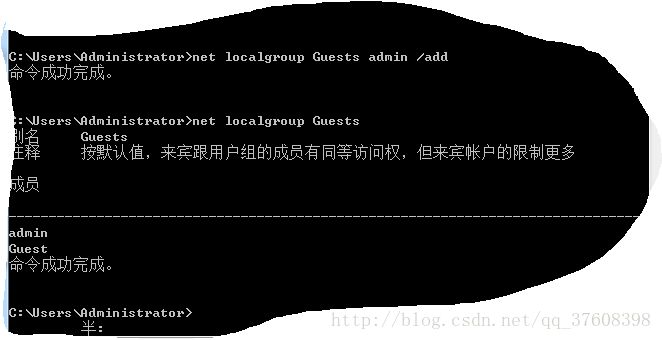
admin を administrators グループに追加するコマンドです。
コマンドを実行する前に
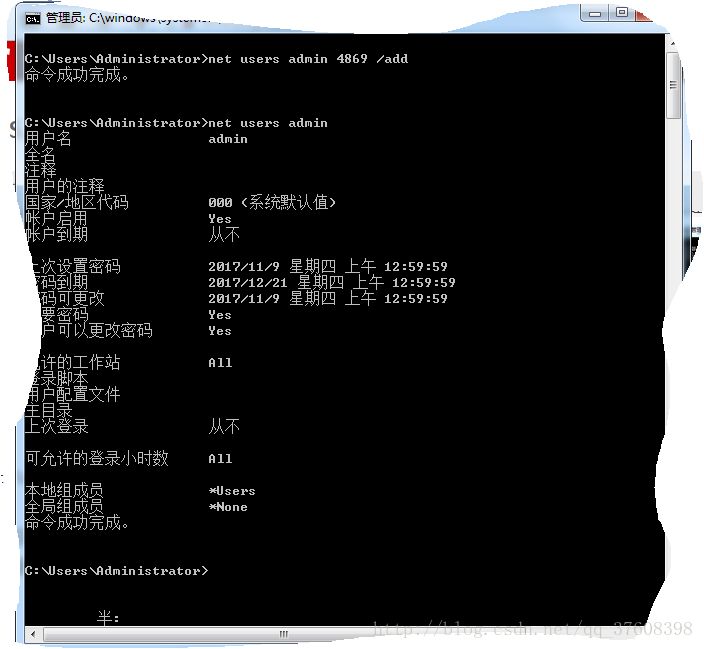
コマンドを実行した後
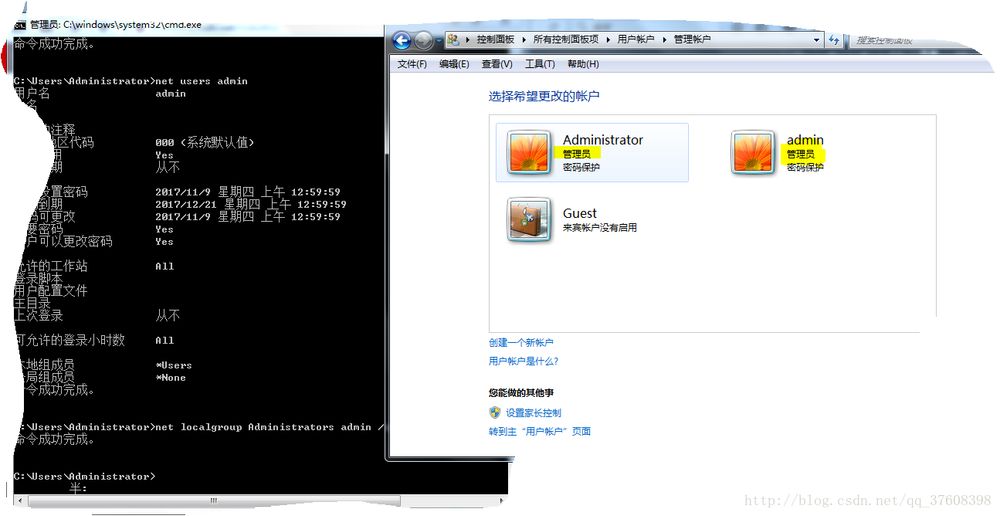
黄色の部分は、先ほどの標準ユーザーから管理者ユーザーに変わるので、ご覧ください。
2. netコマンドの展開
まず、dosのnetコマンドの説明から始めましょう
このコマンドの構文は、:
net localgroup
net localgroup Adminstrators admin /del
ユーザーグループの表示
net localgroup [usergroup name] admin /add
このコマンドは、administrators グループから admin を削除し、admin を標準ユーザーグループとします。
net localgroup [usergroup name] admin /add
グループにadminを追加、グループによって権限が異なる
以上が今回の記事の全内容ですが、皆様の学習のお役に立てれば幸いです。また、スクリプトハウスをより一層応援していただければ幸いです。
関連
-
単語頻度統計(繰り返し行数/各行繰り返し回数)用バッチコード
-
batの一括出力でコードが乱れる問題の解決
-
Windowsのクリップボードに文字列や日付を出力するバッチ処理
-
cmd 環境変数コマンド set 永続的な環境変数の設定 コマンド setx
-
cmdコマンドのリダイレクト出力 2>&1 解説
-
Windowsのcmdコマンドラインの入出力リダイレクト問題
-
バッチ式再帰計算の実装コード N!
-
フォルダバット内の全ファイルの個数と合計サイズの一括統計処理
-
DOSのバッチ構文における%~dp0などの拡張変数について解説します。
-
DOS共通コマンド(echo, rem, cd, dir)の一括処理マニュアル
最新
-
nginxです。[emerg] 0.0.0.0:80 への bind() に失敗しました (98: アドレスは既に使用中です)
-
htmlページでギリシャ文字を使うには
-
ピュアhtml+cssでの要素読み込み効果
-
純粋なhtml + cssで五輪を実現するサンプルコード
-
ナビゲーションバー・ドロップダウンメニューのHTML+CSSサンプルコード
-
タイピング効果を実現するピュアhtml+css
-
htmlの選択ボックスのプレースホルダー作成に関する質問
-
html css3 伸縮しない 画像表示効果
-
トップナビゲーションバーメニュー作成用HTML+CSS
-
html+css 実装 サイバーパンク風ボタン